Chain exploitation of XSS

Hello, friend!
Today I would like to tell you about one interesting chain of low-impact vulnerabilities, which led me to exploitation of full XSS. Also, at the end of the article I will show you an HTML-page that was the final exploit. In order to execute the reflected XSS, I’ve used together vulnerabilities such as ClickJacking, CSRF and self-DOM-based XSS.
Well, let’s start! It was a private program with a little scope. In fact, there was a typical online shop. Since the scope was small, I’ve decided not to report vulnerabilities which were quick for finding and easy for exploitation. In this shop was one feature - you could customize your good before ordering. For example, you could order a T-shirt with your print. Let’s take the situation with ordering a customized T-shirt as an example for this article.
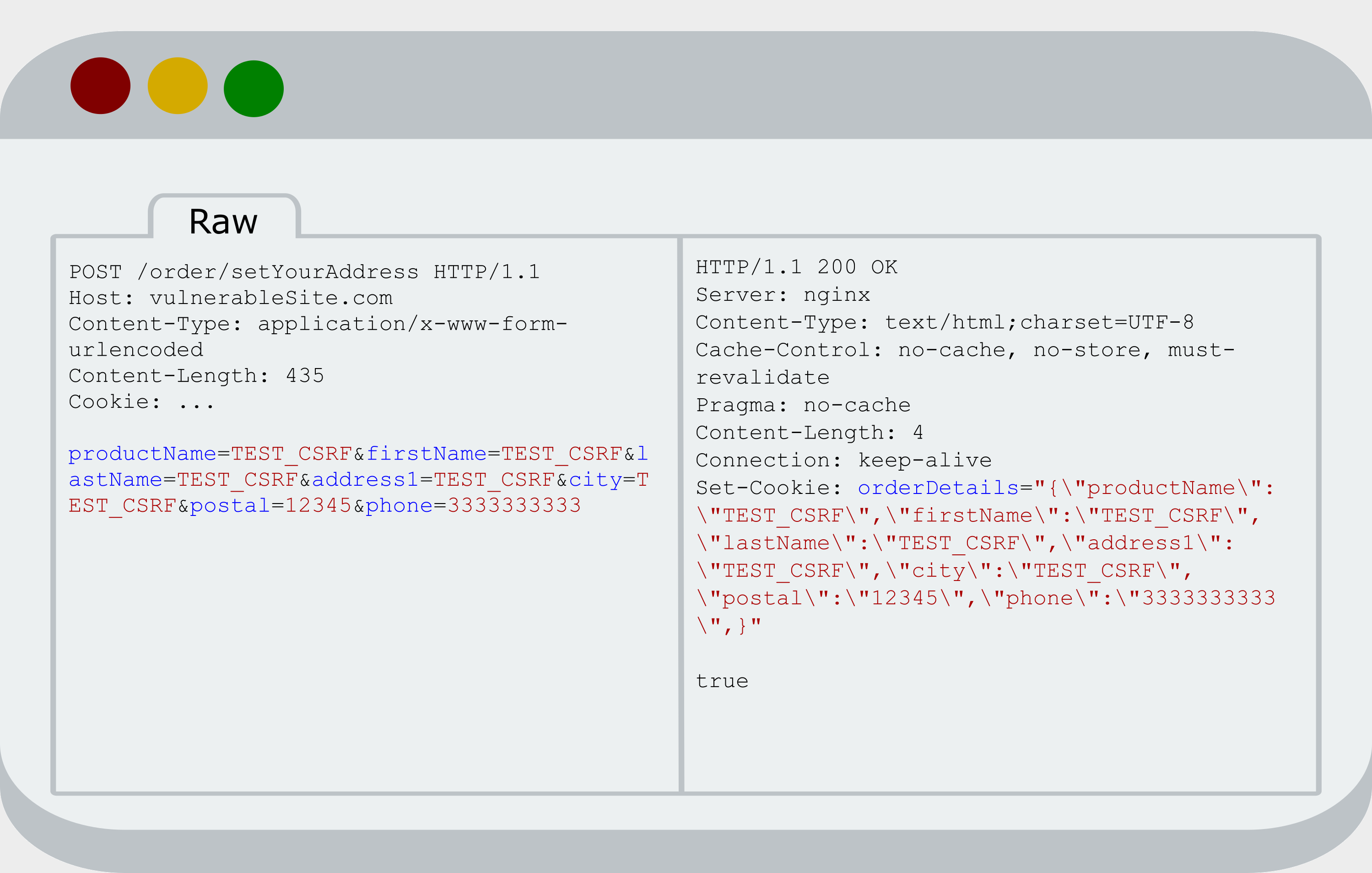
I tried to pass all the steps to order the product (selecting T-shirt color, uploading my own print and filling in customer information). In the last step, I was asked to specify the delivery address. The address has been filled out and the form has been submitted. On this step I noticed that server answered on my POST request with Set-Cookie header with address in JSON format.
I thought it was exploitable CSRF to set the address, but it turned out that there wasn’t. When you go to any page of the site, which is not a step in ordering goods, this cookie value will be removed. In addition, you must have started the customization of your T-shirt and only after this you could set the address via CSRF. Exploitation of this vulnerability was unlikely, so I continued to search for other vulnerabilities.
Quite often, I look through the JS-files in manual mode in order to better understanding how the site works and find new functionality. This site is no exception. Analyzing one of the JS-script, I stumbled on part of source code in which I saw that data were taken from cookie and inserted into DOM-tree without any filtration. As it turned out, this happens when adding the address at the last stage of ordering goods. I didn’t check for the presence of XSS in that place by the BlackBox method, because I thought that the probability of exploitation was small. So, I had a DOM-based XSS in the delivery address and CSRF to setting the same address. It would seem that nothing prevents the exploitation of CSRF + XSS and redirecting the victim to the page where XSS is presented. But, first of all, you cannot go to the last stage of ordering goods (you must pass every stage), and secondly, JS code must set the cookie value when user clicks on button at the very beginning (this cookie was an indicator of the beginning of product customization).
So, I had to hope that this site is not protected from Clickjacking, or somewhere there is an opportunity to set an arbitrary value for cookies. I was lucky and there was no X-Frame-Options header. After that, it became clear that by connecting all these vulnerabilities, we get a 100% exploitable Cross Site Scripting vulnerability.
Shortly, what will happen when a victim opens an HTML page with an exploit:
- In the frame_1, the page where the button to start order construction is located is loaded. The frame is transparent, so it is not visible.
- After the victim clicks on the text “Click me”, a request will be sent, which signals the beginning of customization of the goods and immediately loads the frame_2 for exploitation of CSRF and sends the form from this frame.
- In the HTML adds a picture with a link to the first step to simulate that the victim came to the first step.
- In the HTML adds a picture with a link to the second step to simulate that the victim came to the second step.
- Redirect to the page displaying the address, which is vulnerable to DOM-based XSS.
After that, I wrote a final exploit, which, to my luck, ran like clockwork, and sent a report. I want to notice that the HTML file that is available to you has been changed, since this program is private. Also, I am sure that this exploit can be done better, but I made it that way and it worked. I didn’t change it or make it more beautiful, so you will see it as it was originally.
PoC which was sent by me:
Look for interesting bugs and tell about them! See ya!